Hello, world!
This was another week full of interesting ransomware news. Australian logistics company Toll Group fell victim to a ransomware attack for the second time this calendar year and lost their CIO.
…and that’s not all that happened in ransomware this week!
Ransomware in the News
Toll Group having a bad time
Earlier this year, we talked about Mailto/Netwalker, the ransomware strain that hit Toll Group in February. On May 5, 2020 Toll Group notified customers that select IT systems were proactively taken offline in response to a ransomware incident. In the post, Toll asserts that this is “unrelated to the ransomware incident” from earlier this year. Read the entire series of updates on Toll Group’s website. The restoration effort continues as of this writing, almost a week after the incident was discovered. Toll Group’s updates goes on to identify Nefilim as the ransomware strain involved in this most recent incident. This is the only silver lining in this story; a repeat incident tied the same ransomware strain would be worse.
Making Matters Worse: Instability In Times of Crisis
The ability of a leader to have an impact, whether positive or negative, is often heightened during times of crisis. Spring 2020 brought two crises to the team at Toll Group: COVID-19 and the March 2020 ransomware incident. Under those circumstances, a steady hand would be appreciated by Toll. On May 3rd, it was announced that the Toll Group CIO was leaving Toll for Tabcorp, an Australian gambling entertainment company. According to the timeline, the ransomware incident was discovered by Toll Group the very next day. iTnews carried the story Toll Group CIO jumps to Tabcorp.
tweet 1257164844807016448
Read More
Read more about this story over at The Register or iTnews, where the story broke.
Dakota Carrier Network
This is the first of a few references to Maze this week. DCN, Dakota Carrier Network, fell victim to a Maze ransomware attack. DCN is North Dakota’s leading broadband service provider. DCN’s CEO told local news station KFYR about the attack:
We determined that no customer data that resides on our network was impacted. It was really just DCN’s administrative data, like our in-voicing systems or circuit inventory system and our network management tools that that we use to monitor the utilization of internet bandwidth in the state.
The story from KFYR has more info: DCN hacked by national ransomware gang, customers not affected.
READ North Dakota government fiber provider hit by ransomware over at StateScoop.
About
Was the ransom paid?: No
Ransom Amount: unspecified
Entry Vector: malicious email (per KFYR TV)
Ransomware and Health Care Providers
The relationship between ransomware actors and health care providers has been a topic of conversation given the global response to the continuing coronavirus pandemic. The latest entry in this tale came courtesy of Brian Krebs, who broke a story about a a Snake ransomware incident over at Fresenius, a large private hospital operator in Europe. BleepingComputer puts this incident into context.
Ransomware Round-Up
- Meet NEMTY Successor, Nefilim/Nephilim Ransomware
- Sodinokibi ransomware can now encrypt open and locked files
- Cognizant expects to lose between $50m and $70m following ransomware attack
- Redcar council cyber-attack: 90% of systems working
- REvil ransomware threatens to leak A-list celebrities’ legal docs
- Europe’s Largest Private Hospital Operator Fresenius Hit by Ransomware
- Large Scale Snake Ransomware Campaign Targets Healthcare, More
- LockBit ransomware self-spreads to quickly encrypt 225 systems
- Vcrypt ransomware brings along a buddy to do the encryption
- Taiwan’s state-owned energy company suffers ransomware attack
- Mobile ransomware that doesn’t ask victims for crypto emerges
- New Breed of Ransomware Threatens to Expose Victoria’s Secrets
- Navigating the MAZE: Tactics, Techniques and Procedures Associated with MAZE Ransomware Incidents
The last link is a FireEye blog post that describes how Maze’s TTPs have changed over the course of the last year of observation. The evidence presented results in a picture of Maze as a distributed team, with folks specializing in different areas and getting a percentage of the take in return for their expertise. This post is top-notch and includes samples of actual artifacts. Worth the time!
Ransomware Tweet of the Week
tweet 1256266688800096266
See the tweet on Twitter.
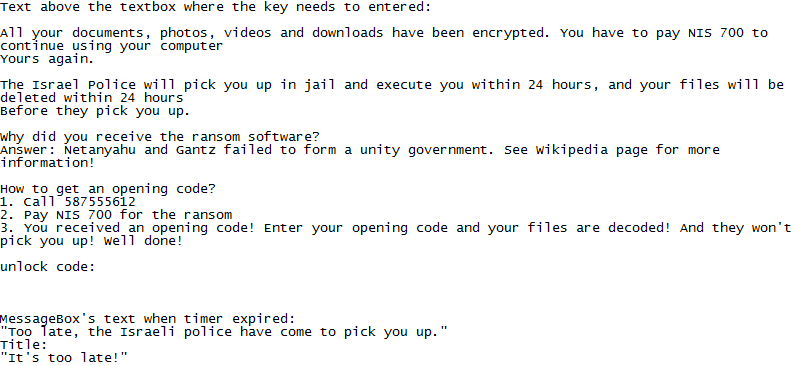
/etc
blackarrowsec/malware-research
I love being able to link to a relevant git repository in the Ransomware Roundup! This repo includes some initial work to stop strains of Ragnarok ransomware. Thanks to blackarrowsec on GitHub:
https://github.com/blackarrowsec/malware-research
README
An interesting read for the week: Ransomware targeting automobiles [PDF]
Contextual Note: This paper describes the various ways that attackers might look to IVI (in-vehicle infotainment) systems as targets for ransomware. The paper provides some discussion traditional IT security metrics and how these differ with respect to automobile security. The lifespan of automobiles is long compared to that of traditional IT systems. The longevity of medical equipment and systems is a complicating factor for those defending health care systems. This SecurityBoulevard article is quick primer on the topic: The journey to better medical device security: Still slow, still bumpy.
Speaking of Maze
Mark your calendar for an upcoming FireEye webinar about Maze on Thursday, May 21, 2020 at 11AM Eastern. It looks like it will be available on-demand after the fact if you can’t make the date and time. Since we are talking about Maze again this week, I thought I’d throw in a link to this SentinelOne write-up:
Maze Ransomware Update: Extorting and Exposing Victims
A closer look at ngrok
The FireEye article Navigating the Maze, linked above, mentions that the Maze crew uses ngrok to tunnel RDP. Like many tools, ngrok can be used for good or ill. It is worth taking a look if it’s new to you.
From <title> on the ngrok website, ngrok.io:
ngrok - secure introspectable tunnels to localhost
…but what does that mean?
A simple use case:
You use Hugo to create your blog. When you run hugo server, the site is available at https://localhost:1313. However, you want a friend who is elsewhere who wants a sneak peek. You can tell Hugo to bind to 0.0.0.0 and modify your network setup as appropriate or you can use ngrok! Once Hugo is up and listening, run ngrok http 1313.
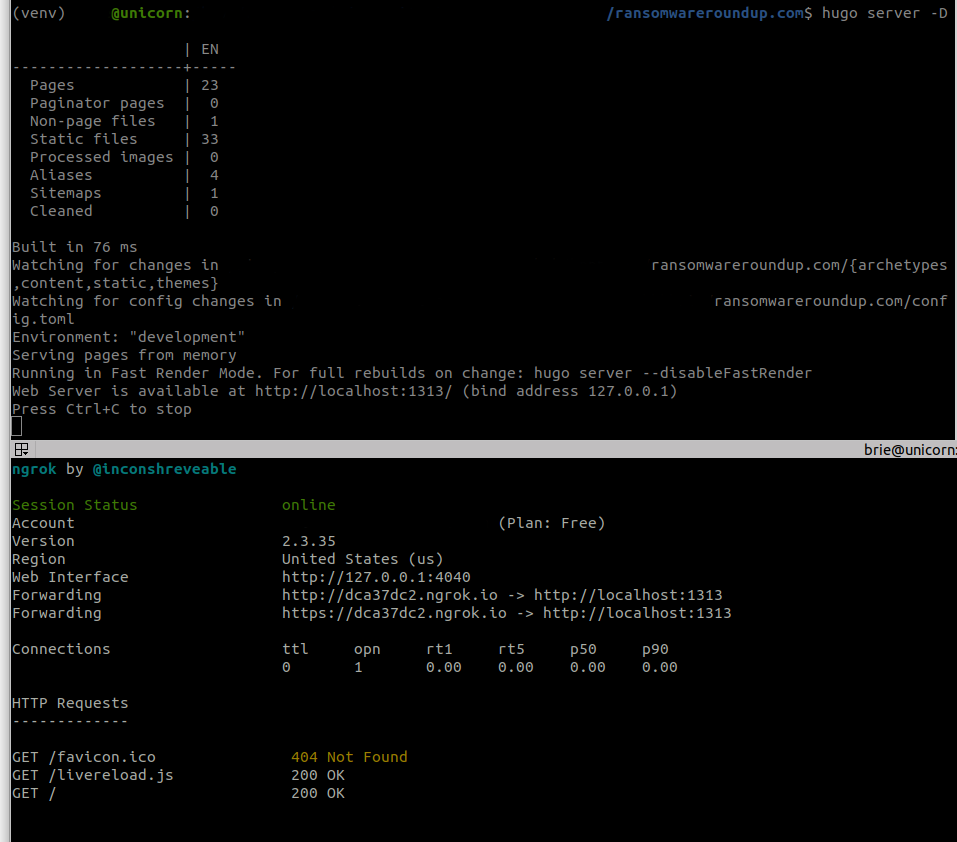
The tunnel will be set up and you’ll see the URL that has been generated and a status screen that lets you see information about requests to your site. The screenshot above shows the hugo server status results in the top pane and the ngrok status information in the lower pane. Send the *.ngrok.io URL to your friend.
There is alpha grade support for self-hosting ngrok: SELFHOSTING.md. (This looks like a good candidate for an Ansible role.)
yara v4.0.0
This technically belonged in last week’s issue but it’s too good to miss: there is a brand new major version of Yara available!
There are backward-incompatible Yara API changes that are detailed here. The addition of the --scan-list option should be a nice improvement.
FIN
Be well.