Hello, world!
Welcome back to the Ransomware Roundup! While the novel coronavirus continues to dominate headlines across the world this week, ransomware was not to be left out! This issue includes some original reporting about CovidLock, the mobile ransomware aiming to profit from people seeking information in these uncertain times.
Let’s get started!
Ransomware in the News
Mailto/Netwalker Returns
Mailto/Netwalker is the strain of ransomware that has impacted Toll Group, the Australian logistics company last month. On Thursday, March 12, the Champaign-Urbana Public Health Department fell victim to Mailto, per StateScoop. The timing of this attack is especially significant given that the Web site is an important source of information for residents of the county seeking information about the health department’s response to the threat posted by COVID-19. This prompted a write-up by The Register.
While their website was down, the health department demonstrated that they have redundant means of communication with the community. They continued to provide updates on Facebook and Twitter, including the following:
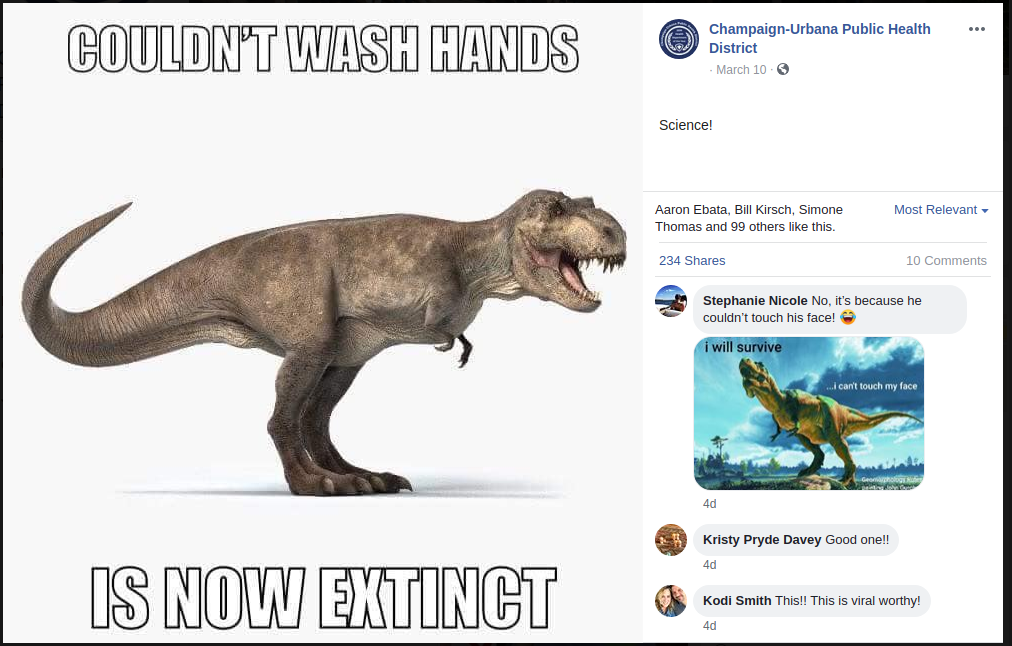
The public-facing portion of the outage was fairly short-lived. The next day, the website was restored.
CovidLock
Security researchers at DomainTools have a brief write-up of a new strain of mobile ransomware targeting Android users who visit hxxp://coronavirusapp[.]site and agree to download the ‘Coronavirus Tracker’ app. The DomainTools Security research team has committed to posting the decryption key publicly as well as releasing further technical details but have not done so at the time of publication. Rather than wait, I obtained a copy of the .apk and inspected it further myself. Here is what I learned:
About Coronavirus Tracker
Summary: This is a hasty slapdash attempt at ransomwaring already frightened people. Calling this “ransomware” demonstrates the range of complexity and sophistication that various attacks can have. I performed static analysis on the app and ran it in Android Studio in order to learn more about it. It is the kind of ransomware that blocks the user’s ability to user the machine by repeatedly displaying a lock screen taht demands a ransom.
How it works:
- Visit hxxp://coronavirusapp[.]site
- Click the link to download CoronavirusTracker (It is a
bit.lylink that was created on March 10th.)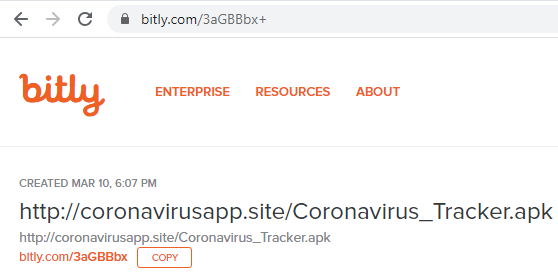
- Install the app
- The user will be required to grant the app a set of permissions before the app will allow the user to scan their area for coronavirus
- Once the permissions are granted, the app displays a ransom note
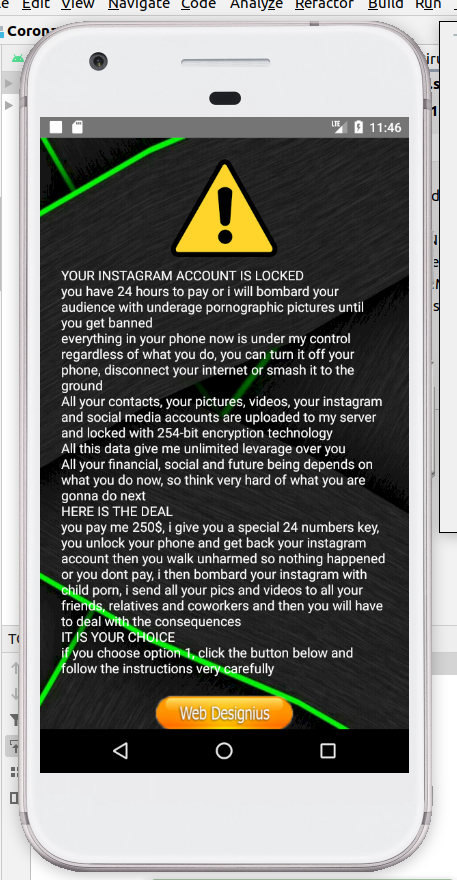
- Clicking the button takes the user to a paste on Pastebin with more information. Here is a clone of the original paste.
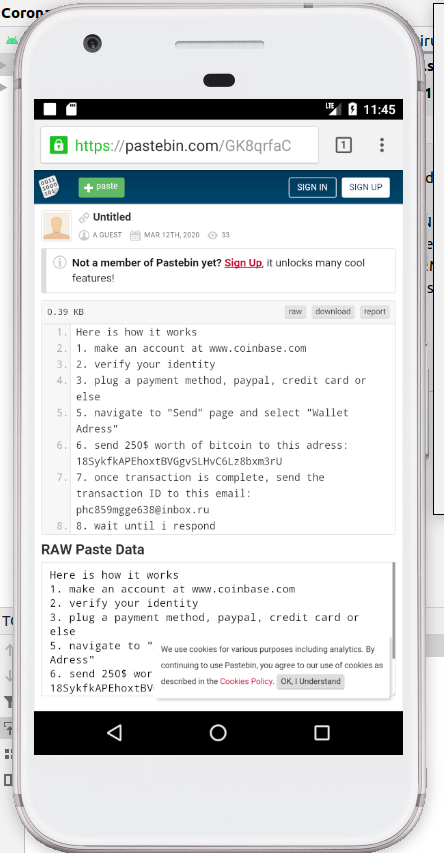
- The Bitcoin wallet address in the Pastebin link is
18SykfkAPEhoxtBVGgvSLHvC6Lz8bxm3rU - Once the Bitcoin has been sent, the victim is to send the transaction ID by email to
phc859mgge638@inbox.ru - The user is provided with a decryption code that they can give to the lock screen
As of this writing, that address has yet to receive any funds.
Watch the app at work on YouTube
Hash
MD5: 1602c0258f39b2b032edd7d6160befe7
SHA256: 1b72847f42d4fc1296f7c4c1955523fc4cc7a323dbad6b3be5d94496c7f82e23
About
Was the ransom paid?: No
Ransom Amount: **$100-$250 **
Ransom Currency: BTC
Ransom Time: 48 Hours
Entry Vector: User installs .apk file from website and grants many permissions to it
The Ransomware Roundup
Other ransomware happenings this week include:
- Two ‘Russian’ Ransomware Attacks Take Down North Carolina City And County Government Systems
- New CoronaVirus Ransomware Acts as Cover for Kpot Infostealer
- Paradise Ransomware Distributed via Uncommon Spam Attachment
/etc
Brian Krebs has penned a piece entitled Live Coronavirus Map Used to Spread Malware.
The real time coronavirus map by Johns Hopkins is located at https://coronavirus.jhu.edu/map.html.
The subreddit for coronavirus information is /r/coronavirus at https://www.reddit.com/r/Coronavirus/.
FIN
Stay safe.
Wash your hands.
Be kind to one another.