Hello, world!
The biggest story in ransomware news this week was an update on the Travelex ransomware incident discovered on New Year’s Eve 2019.
Ransomware in the News
WSJ: Travelex Paid Hackers Multimillion-Dollar Ransom Before Hitting New Obstacles
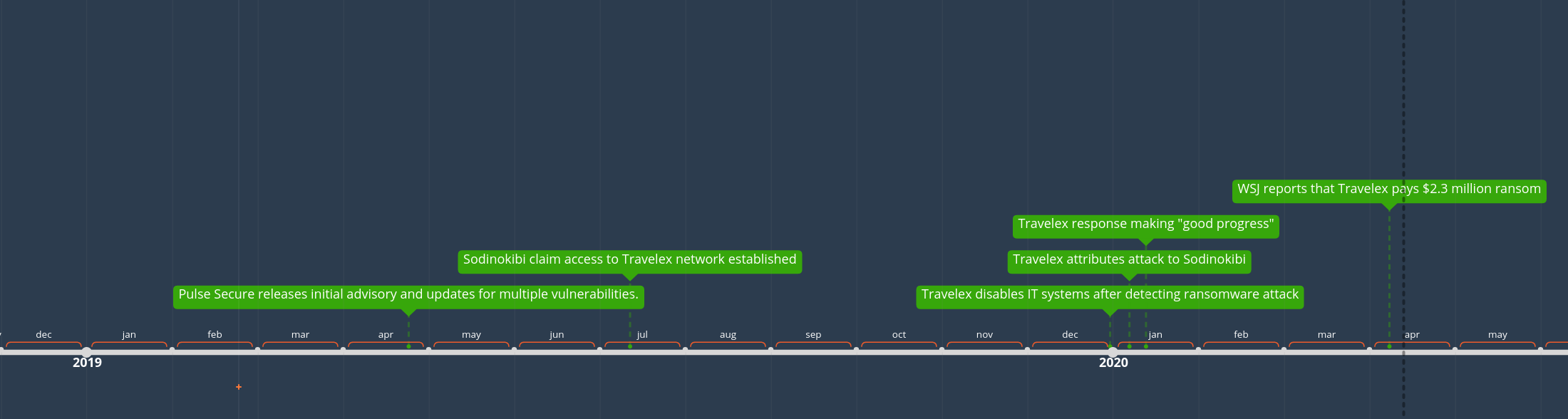
WSJ reports that Travelex paid aproximately $2.3 million in ransom demands. Read the story on wsj.com. Immersive Labs has a good timeline of the Travelex incident from 31 December to January 8th. The timeline below gathers key details for a quick summary (zoom in):
About
Was the ransom paid?: Yes
Ransom Paid: ~$2.3 million
Entry Vector: vulnerable Pulse Secure VPN
There’s a repository containing proof of concept code for the Pulse Secure VPN vulnerability with CVE 2019-11510. This is a shell script that clarifies the nature of the vulnerability. This is a directory traversal vulnerability that lets a remote unauthenticated attacker cat files.
Speaking of Sodinokibi
Sodinokibi claims that they will cease accepting Bitcoin and request ransom payments be made in Monero instead. This move is designed to make tracking ransomware payments more difficult. Bleeping Computer has more.
An Algerian state-owned oil company gets ransomwared
Under the Breach @underthebreach reported on April 4th that Maze had exfiltrated data from Sonatrach and posted it on their site. Sonatrach is a 57 year-old Algerian state-owned gas company that has sufferd instability for the last few years. Sonatrach has had four CEOs in the last year, for example.
“Abdelmoumen Ould Kaddour was replaced as the CEO of national oil company Sonatrach by Rachid Hachichi. Hachichi was replaced in November 2019 by Chikhi Kamal-Eddine, who was replaced by Toufic Hakkar in February 2020. This turbulence parallels the uncertainty of Algeria’s upstream sector and Hakkar, Sonatrach’s fourth chief executive in less than a year, will have challenges to face to stabilise the company’s production.” Source: OilandGasMiddleEast.com
More stories about Sonatrach for the interested:
- February 2020: Algeria names new chief for state energy firm Sonatrach: state TV
- November 2019: Chikhi takes office as Sonatrach CEO
- August 2018: Algeria’s state oil firm gets new management, targets brain drain
Bleeping Computer has a list of new ransomware variants identified this week
Ransomware Round-Up
- Cybercriminals targeting critical healthcare institutions with ransomware - advisory from Interpol
- Analyzing & Decrypting L4NC34’s Simple Ransomware
- Coffee Co. Jail target of ransomware attack
- Travelex Reportedly Paid $2.3 Million Ransom to Restore Operations
- Fintech Company Survived Ransomware Attack Without Paying Ransom
/etc
Ransomware Stock Photos
Just for some fun, let’s look at some examples of ransomware stock photography. Courtesy of the Air Force Reserve Command comes this photo “depicts the act carried out by ransomware”.
Here are some fun ones from the FBI:


FIN
Until next time!
